TLS between clients and the Connector
The hostname you configure will be used to reach and use your Connector. It can be managed by Formal or by yourself.- Formal-Managed: The hostname is a subdomain of a domain that belongs to Formal. Formal will create and renew the TLS certificate of your Connector.
- Customer-Managed: The hostname is in a DNS zone you control. You are responsible for configuring your DNS records and managing your TLS certificates.
Note for Mac users: If you’re connecting to a Connector over HTTP/TLS using
curl on macOS, you may need to install curl via Homebrew (brew install curl) as the native curl installed on Mac does not support newer versions of TLS.Formal-Managed
Formal will automatically generate and renew the TLS certificate for your Connector if the hostname ends with.[NAME_OF_YOUR_ORG].connectors.joinformal.com.
Using our Terraform provider, you can create such a Connector hostname and precise where it should point to:
Customer-Managed
For self-managed hostname and TLS, you must provide your TLS certificate to the Connector. You can do so via our APIs, Terraform, or the Formal console: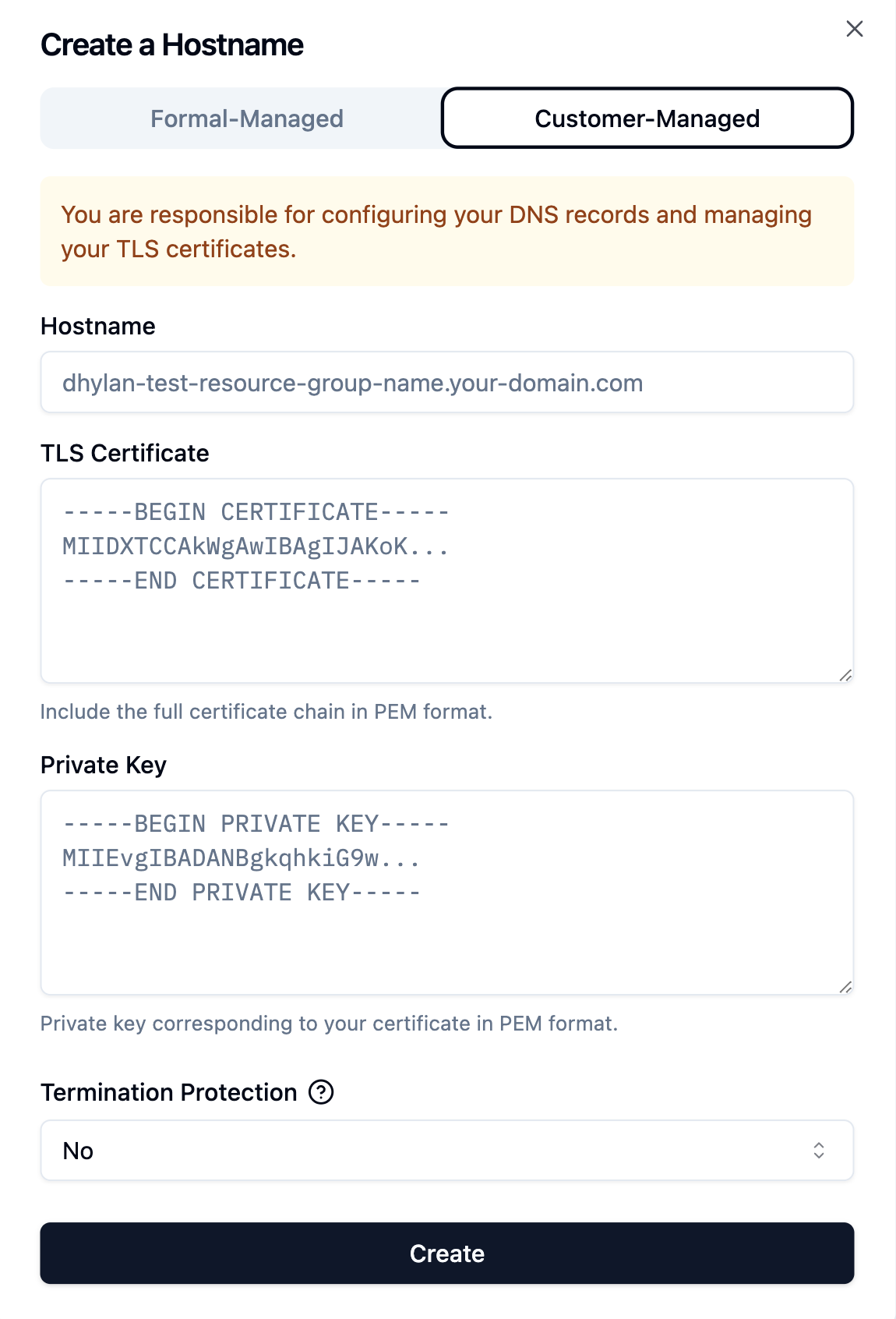
TLS between the Connector and Resources
You can configure TLS settings between the Connector and resources on an individual resource level via our APIs, Terraform, or the Formal console: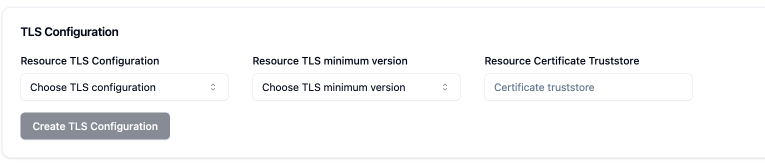
disable, insecure-skip-verify, insecure-verify-ca-only (verifies certificate chain but not hostname), or verify-full.