Overview
The Formal Connector operates by reverse-proxying the S3 API, effectively serving as an intermediary that forwards requests to S3. By reverse-proxying all buckets that the configured IAM role has access to, it enables precise control over bucket access and operations. Users can specify the target bucket when using the AWS S3 CLI/API, ensuring that access is streamlined and secure.Creating an S3 resource
Using the S3 Connector requires a hostname to be configured. See Hostname and TLS Configuration for more details.
ListBuckets API call. For example, for AWS-hosted S3, you should use s3.amazonaws.com as your resource hostname. For Cloudflare R2, you should use <ACCOUNT_ID>.r2.cloudflarestorage.com.
Authentication
S3 Resources do not support Native Users. For S3, the Connector automatically uses AWS credentials provided via the Instance Metadata Service (IMDS), environment variables, or Pod Identity. See the AWS S3 documentation for more details on S3 authentication.
Autodiscovery of S3 buckets
The Formal control plane can autodiscover S3 buckets in your AWS account. Please see Cloud Integrations to enable autodiscovery for a given account.Connecting to S3 via the Connector
Using the AWS CLI
To connect to S3 via the Connector, you should use your Formal Credentials as your AWS Credentials and modify the endpoint url to the Connector hostname as follows:Using the Formal Desktop App
The Formal desktop app streamlines S3 access by seamlessly routing S3 CLI commands to the connectors that can best access the requested AWS account and bucket. This feature requires S3 bucket autodiscovery to be enabled for all AWS accounts that host buckets that users might access via the desktop app. Examples of commands via the desktop app are below.Using the Formal S3 Browser
The Formal S3 Browser is a web interface embedded in the connector that allows you to browse, upload, and download files from your S3 buckets. To use the S3 Browser, you can navigate tohttps://<connector_hostname>:<port>/formal-s3-browser in your web browser. You will then be redirected to the Formal console which will automatically authenticate you to the connector and make the S3 Browser available to you.
After logging in, you’ll first be presented with a list of the S3 buckets accessible to your connector.
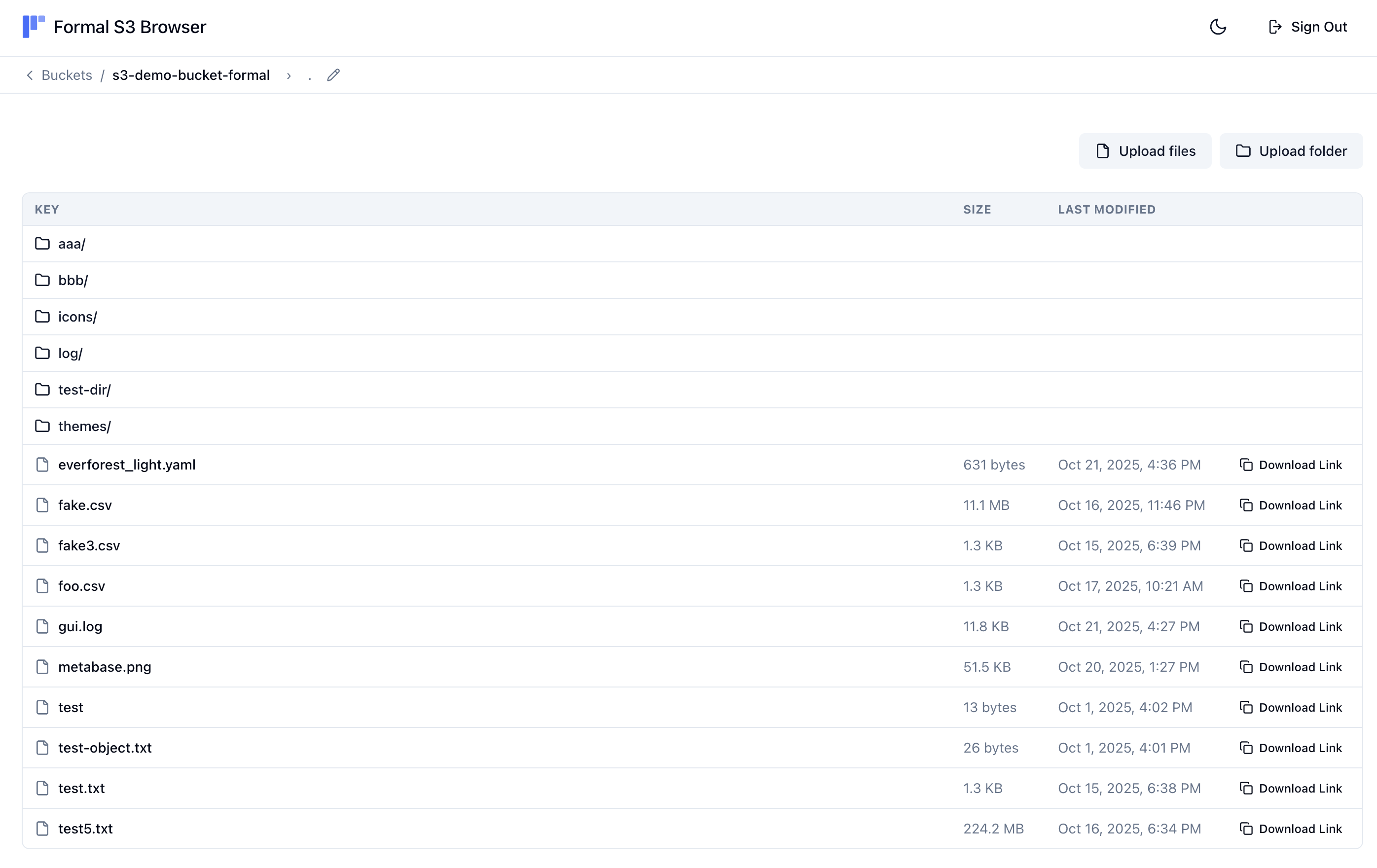
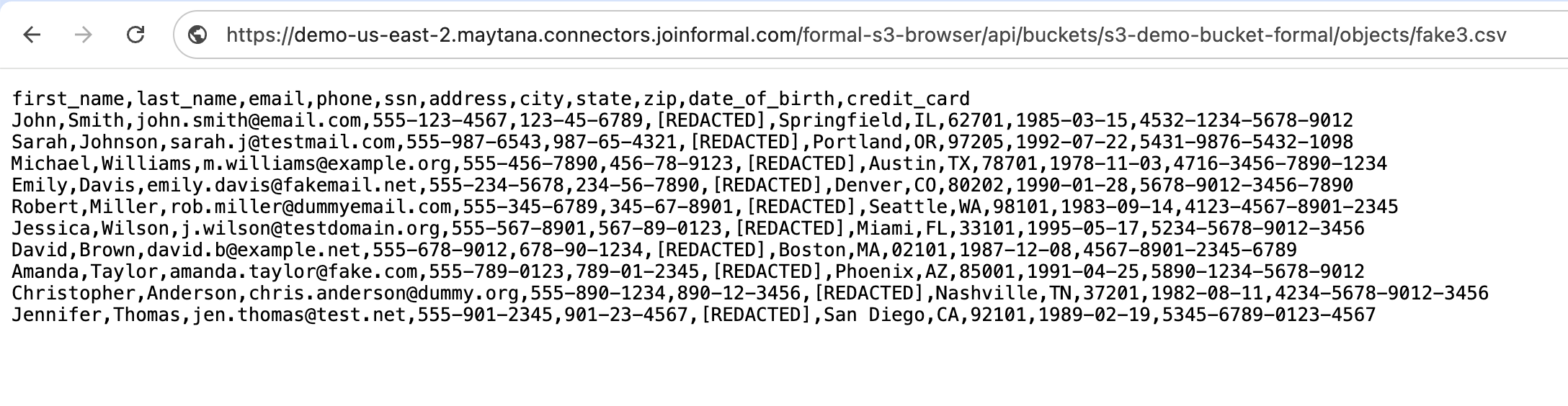
GetObject requests, the S3 Browser will also mask the contents of the file on download.
End-user identity propagation
The S3 connector supports end-user identity propagation for internal applications and BI tools. For S3, the connector relies on the HTTP headerX-Formal-End-User-Identity to identify the end user by their email. Examples of configuring this for the AWS SDK for various languages are below.
enduser.go
Policy Evaluation
Formal supports the following policy evaluation stages for S3:- Session: Evaluate and enforce policies at connection time
- Pre-Request: Evaluate and enforce policies before request execution